Keycloak Infrastructure Preparation
Introduction
During PoolParty 9.0 installation or upgrade from version 8.1 to 9.0 the Keycloak application will be also installed. By default it is installed as a separate application in the same environment where PoolParty is installed.
Keycloak has its own Web server which listens to port 8181, and the application is accessible at path/auth. Therefore, after a fresh installation, its Web application is reachable at http://keycloak.server.ip.address:8181/auth where keycloak.server.ip.address is the IP address of the server where Keycloak is installed.
Tip
Please refer to Change the Keycloak Port if Keycloak needs to be configured for a different port. This can only be done after the installation!
Keycloak has to be externally accessible by users in a similar way as PoolParty applications, because Keycloak directly receives and processes users authentication and authorization requests.
Consequently, connections to Keycloak should be secured by SSL/TLS to enable HTTPS access.
Note
Before proceeding with PoolParty installation or update, please make sure the following infrastructure configuration has been implemented so that Keycloak is externally accessible.
In modern IT infrastructure HTTP connections without any encryption are not allowed for security reasons; furthermore only a limited number of ports is open in a secure IT environment. It is a common practice today to have a gateway, reverse proxy or load balancer to provide for the exposure of the application's port and encryption to this port. Typical solutions include Nginx for in-house operations, Amazon Elastic Load Balancing (ELB) for AWS cloud infrastructure, Azure Application Gateway for Azure cloud infrastructure. Please refer to the corresponding AWS and Azure documentation for more details related to your cloud infrastructure.
Your infrastructure for Keycloak needs to be appropriately configured so that Keycloak is exposed and externally accessible. The expected outcome of the configuration is that an HTTPS URL such as https://keycloak.domain.name/auth where keycloak.domain.name is the custom domain name configured for the Keycloak application accessible to users and its connections are properly forwarded to and received by the Keycloak application running at http://keycloak.server.ip.address:8181/auth.
HTTPS and TLS termination have to be implemented at the the gateway respectively proxy level using the CA signed certificates associated with the custom domain name for Keycloak so that the connection between external users and the gateway/proxy is secured.
With the aforementioned configuration, the communication between PoolParty and Keycloak, and between Keycloak and the gateway/proxy remains a plain HTTP connection. To implement the highest security standards, it is recommended that end-to-end encryption is implemented for all communication.
Note
Please refer to Security Configuration documentation for more details on how to implement HTTPS at the application backend.
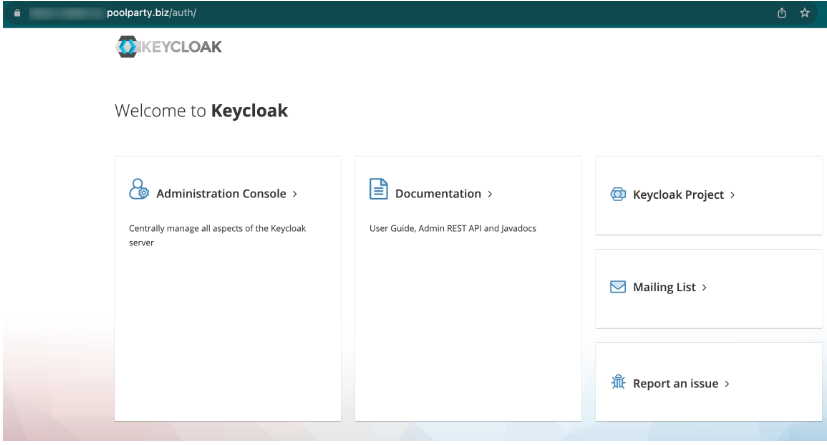
Once Keycloak has been installed and is running and assuming that the configuration is correct, then when a user opens a public Keycloak URL such as https://keycloak.domain.name/auth in their browser, the Keycloak web user interface will be displayed. The screenshot below illustrates a successful access to the Keycloak web interface.
Note
Also note the lock icon next to the URL indicating a secure connection.