Information Security Practices and Procedures
12/01/2026
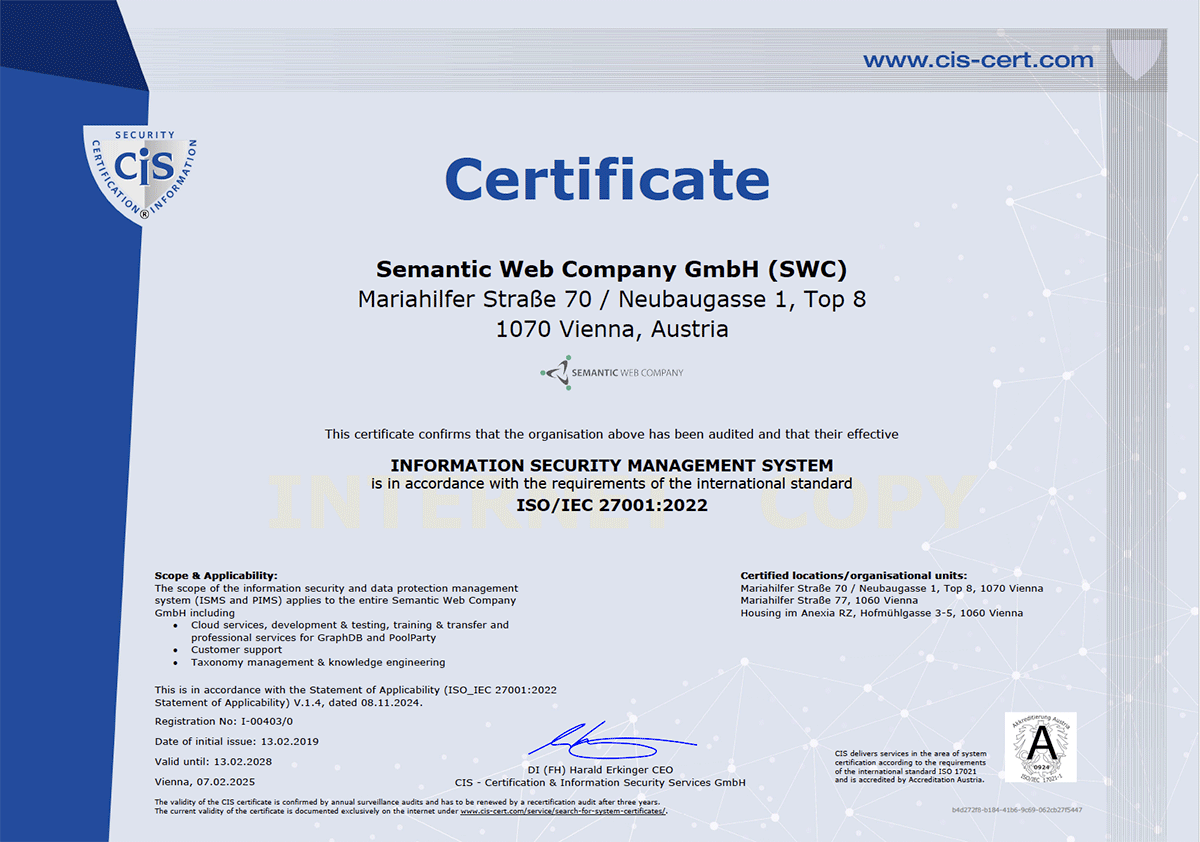
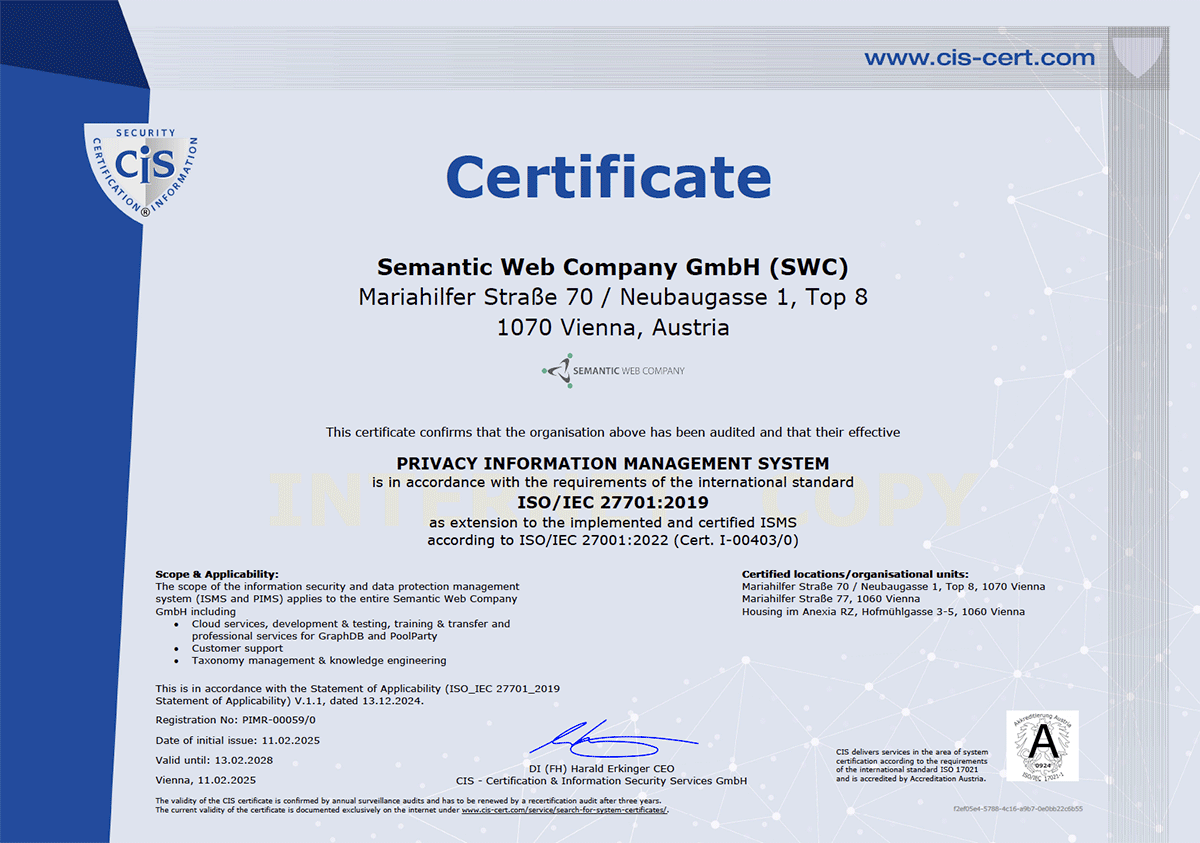
Information security stands as a fundamental cornerstone of the Graphwise group (Ontotext and Semantic Web Company). This commitment is embedded throughout our organizational structure, security policies, and operational processes, and is formally recognized through our ISO/IEC 27001:2022 and ISO/IEC 27701:2019 certifications. These certifications are maintained through rigorous, independent audits conducted by authorized third-party organizations. All Graphwise personnel adhere to comprehensive workplace security protocols, including mandatory incident reporting procedures. Regular security training sessions are conducted for the entire workforce to ensure consistent awareness and compliance.
Graphwise safeguards its infrastructure through robust measures including:
Comprehensive disaster recovery and business continuity planning
Systematic backup protocols for all company data
Thorough logging and monitoring of security-relevant events
Proactive prevention of unauthorized access attempts
Our network security architecture incorporates next-generation firewall technology across all system environments to protect both business operations and client assets. Additional protection is provided through host-based intrusion detection and prevention systems (HIDS/HIPS). Security monitoring includes daily scans of all hosts for file integrity verification and continuous database monitoring for unauthorized modifications.
Software development at Graphwise follows secure-by-design principles and industry best practices, including:
Secure dependency management
Protected source code repositories
Comprehensive vulnerability management
Secure data handling protocols for information in transit and at rest
All source code resides in secured Git repositories with write access limited exclusively to authorized development personnel. JavaScript code undergoes minification for additional protection and remains proprietary.
PoolParty adheres to industry best practices by implementing data minimization principles, exposing only the data necessary for specific purposes and limiting the duration that sensitive information remains in memory or unencrypted. All externally exposed sensitive data is secured using state-of-the-art cryptographic protection, including password hashing via PBKDF2 and encryption of third-party credentials using AES with configurable key sizes that meet current security standards.
PoolParty provides various ways to authenticate users. The default authentication method for the user interface is password-based verification. Administrators can configure a strong password policy. Customers can also leverage their existing access management infrastructure and configure single sign-on. Social login and multi-factor authentication (MFA) come out of the box. Token-based authentication (OAuth 2.0) is implemented for all PoolParty APIs except for UnifiedViews.