Add Role Mapper for LDAP Integration
While configuring an LDAP integration, you need to add a mapper that will assign LDAP users to user roles in PoolParty.
If the users on the LDAP server are assigned to groups with names matching the names of the user roles in PoolParty, you can add and configure a mapper that will assign the users to the corresponding PoolParty user roles (see option 1 below).
If this is not the case, use the default poolparty-default-role-ldap-mapper, which will assign the LDAP users to a placeholder user role None (see option 2 below). Users with this role cannot use PoolParty until a PoolParty SuperAdmin changes their role in the PoolParty User Management.
Make sure that the PoolParty user roles are represented on the LDAP server as follows:
There is an organizational unit (instance of the
organisationalUnitobject class), called for example Roles (1).Under this unit, there are groups (instances of a group object class) representing the individual PoolParty user roles (2).
The
cnattribute of the groups matches the names of the PoolParty roles, for instancecn=PoolPartyUser(3).Users are added to these groups via the
memberattribute (4).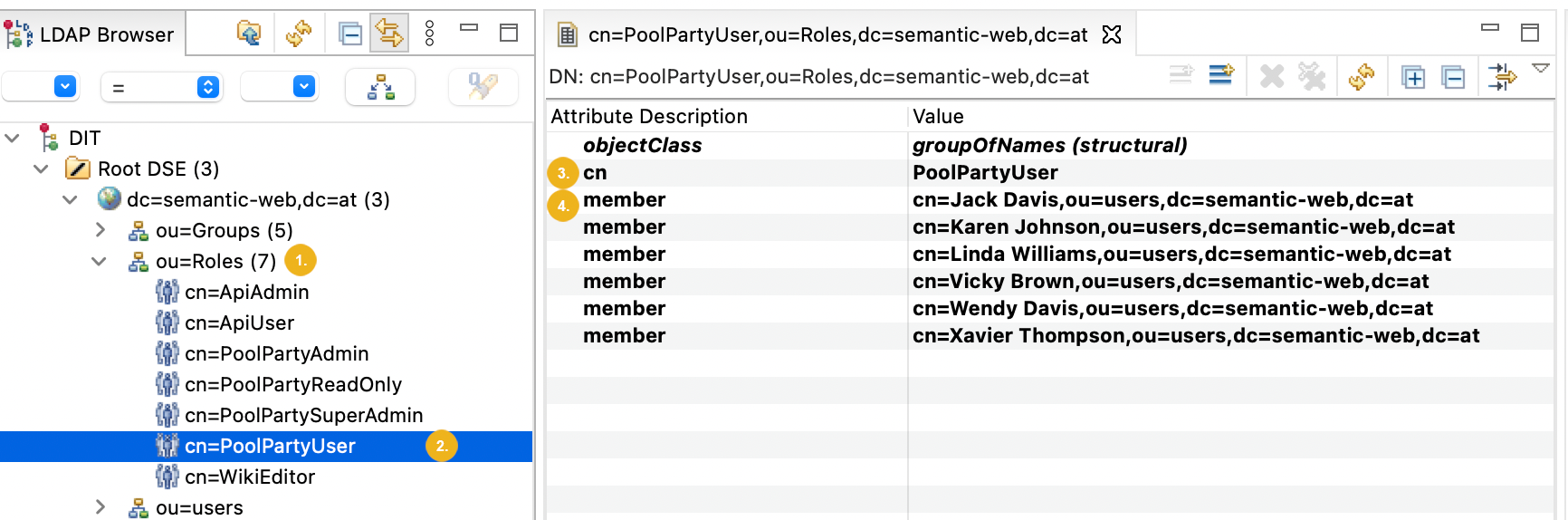
In Keycloak, open the user federation you configured for your LDAP server. For more information, refer to Configure LDAP Integration.
Go to the Mappers tab.
Click Add mapper.
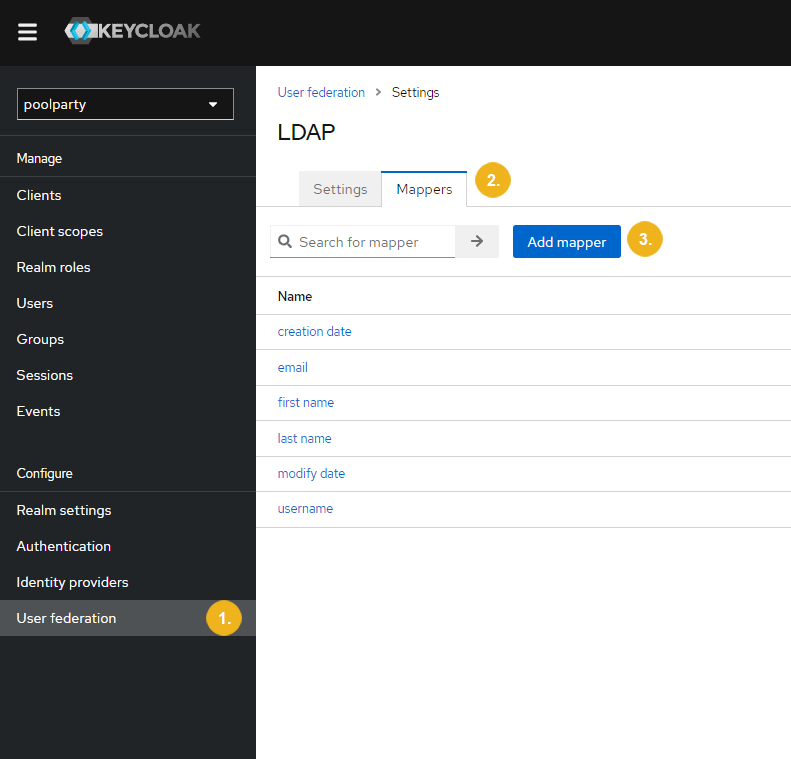
The Add user federation mapper page opens.
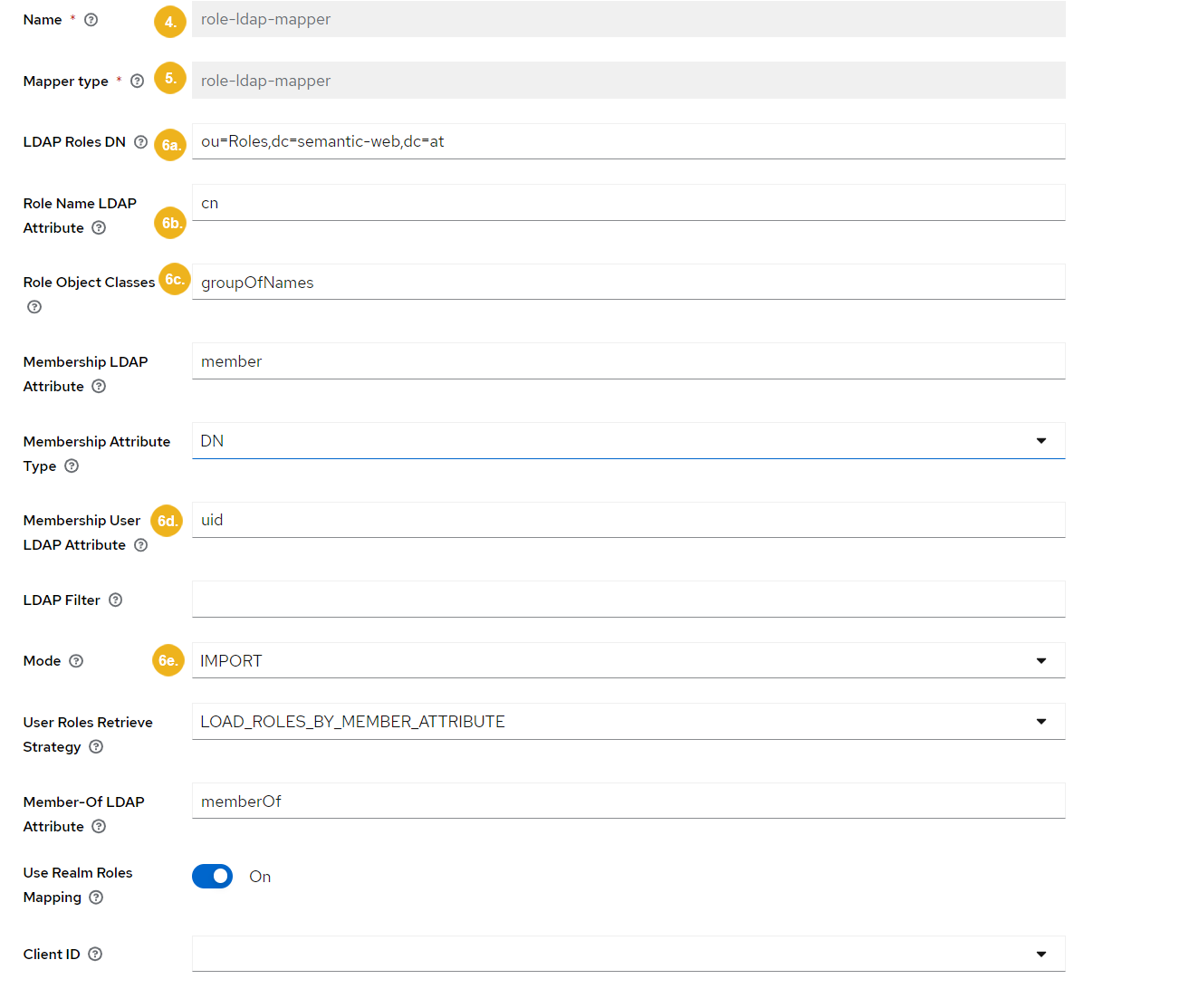
Type in the mapper's name.
Select
role-ldap-mapperas the mapper type.Configure the mapper. These are the most important fields:
LDAP Roles DN: must match the base DN for the roles in LDAP (in our case
ou=Roles, dc=semantic-web, dc=at).Role Name LDAP Attribute: must match the role name attribute in LDAP (in our case
cn).Role Object Classes: the object class for roles, usually is
groupOfNames.Membership User LDAP Attribute: must match the LDAP attribute that maps the user's username (in our case
uid).Mode: must be IMPORT.
Tip
For more information on how to fill in a certain field, hold your pointer over the Help icon in the Keycloak UI.
Confirm with Save.
After initial synchronization, the LDAP users get created in the PoolParty User Management with corresponding roles coming from the LDAP server.
In Keycloak, open the user federation you configured for your LDAP server. For more information, refer to Configure LDAP Integration.
Go to the Mappers tab.
Click Add mapper.

The Add user federation mapper page opens.
Type in the mapper's name.
Select
poolparty-default-role-ldap-mapperas the mapper type.Confirm with Save.
After initial synchronization, the LDAP users get created in the PoolParty User Management with the user role None. This role doesn't allow them to use PoolParty until a SuperAdmin changes it manually. For more information on how to do so, refer to How to Edit Existing Users.
Once a SuperAdmin changes the role of an LDAP user in the PoolParty User Management, their user role doesn't get overwritten by the None user role even if the user gets re-synchronized in Keycloak.