- PoolParty Semantic Suite Documentation
- Administrator Guide
- PoolParty Administration
- PoolParty User Administration Setup Using Keycloak
- Keycloak Infrastructure Preparation
Keycloak Infrastructure Preparation
04/11/2025
The Keycloak application is installed during PoolParty 9.0 installation or when upgrading from version 8.1 to 9.0. By default, Keycloak is deployed as a separate application within the same environment as PoolParty.
Keycloak operates its own web server that listens onport 8181 and is accessible at the /auth path. Following a fresh installation, the web application is reachable at http://keycloak.server.ip.address:8181/auth where keycloak.server.ip.address represents the IP address of the Keycloak server.
Tip
Port modifications are only possible after installation is complete.
Keycloak must be externally accessible to users in the same manner as PoolParty applications because it directly processes user authentication and authorization requests. Therefore, all connections to Keycloak must be secured using SSL/TLS to enable HTTPS access
Note
Ensure the following infrastructure configuration is implemented for Keycloak external accessibility before proceeding with PoolParty installation or update.
Modern IT infrastructure prohibits unencrypted HTTP connections for security reasons, and secure environments typically restrict open ports. Standard practice involves implementing a gateway, reverse proxy, or load balancer to expose application ports and provide encryption. Common solutions include:
Nginx for on-premises deployments
Amazon Elastic Load Balancing (ELB) for AWS cloud infrastructure
Azure Application Gateway for Azure cloud infrastructure
Refer to the official AWS and Azure documentation for cloud-specific implementation details.
Your Keycloak infrastructure must be configured to ensure external accessibility. The expected configuration outcome is an HTTPS URL such as https://keycloak.domain.name/auth where keycloak.domain.name is the custom domain name assigned to your Keycloak application. This URL must properly forward connections to the Keycloak application running at http://keycloak.server.ip.address:8181/auth.
HTTPS and TLS termination must be implemented at the gateway or proxy level using CA-signed certificates associated with the Keycloak custom domain name. This ensures secure connections between external users and the gateway/proxy.
With this configuration, communication between PoolParty and Keycloak, as well as between Keycloak and the gateway/proxy, remains unencrypted HTTP. For maximum security, implementing end-to-end encryption for all communication paths is recommended.
Note
For detailed instructions on implementing HTTPS at the application backend, refer to the Security Configuration documentation.
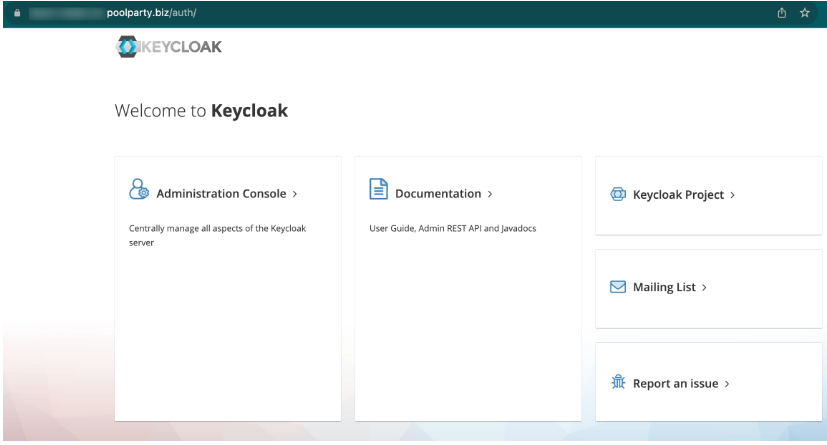
After successful Keycloak installation and proper configuration, users accessing the public Keycloak URL (e.g., https://keycloak.domain.name/auth) through their browser will see the Keycloak web user interface. The screenshot below demonstrates successful access to the Keycloak interface:
Note
The lock icon next to the URL indicates a secure connection.